Which Of The Following Is Not A Component Of A Key Escrow System?
Which of the following is not a component of a key escrow system?. The Diffie Hellman uses a pair of asymmetric keys for. A System administrators should retain user accounts after an employee has been terminated. Is legally insufficient and not recognized by law as a binding contract.
Personal property is not considered an improvement. The scan is performed at a time of day when the vulnerability does not exist. B All employees must be provided with uniform general training on security regardless of the sensitivity of their positions.
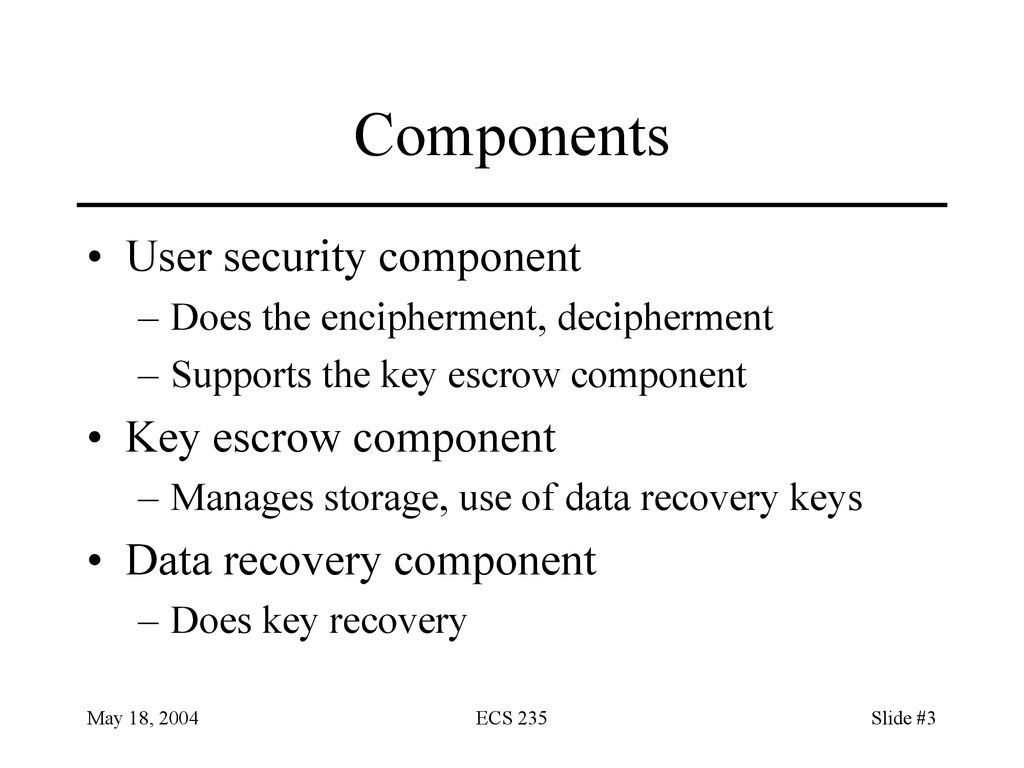
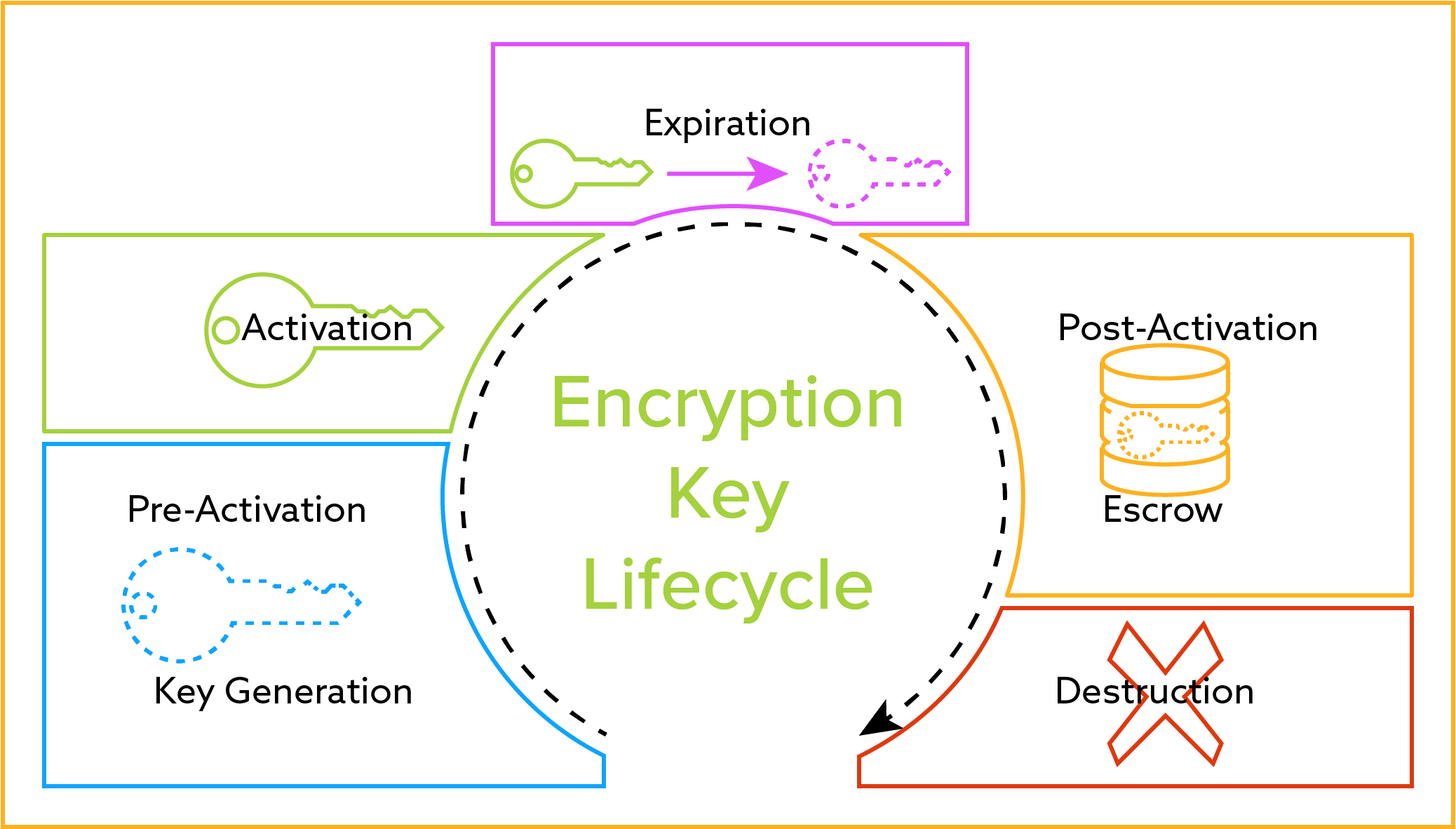
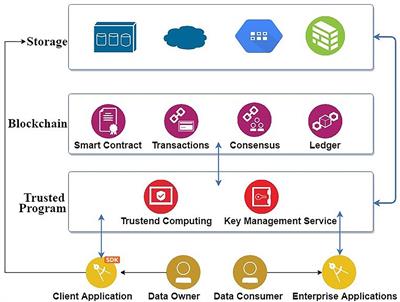
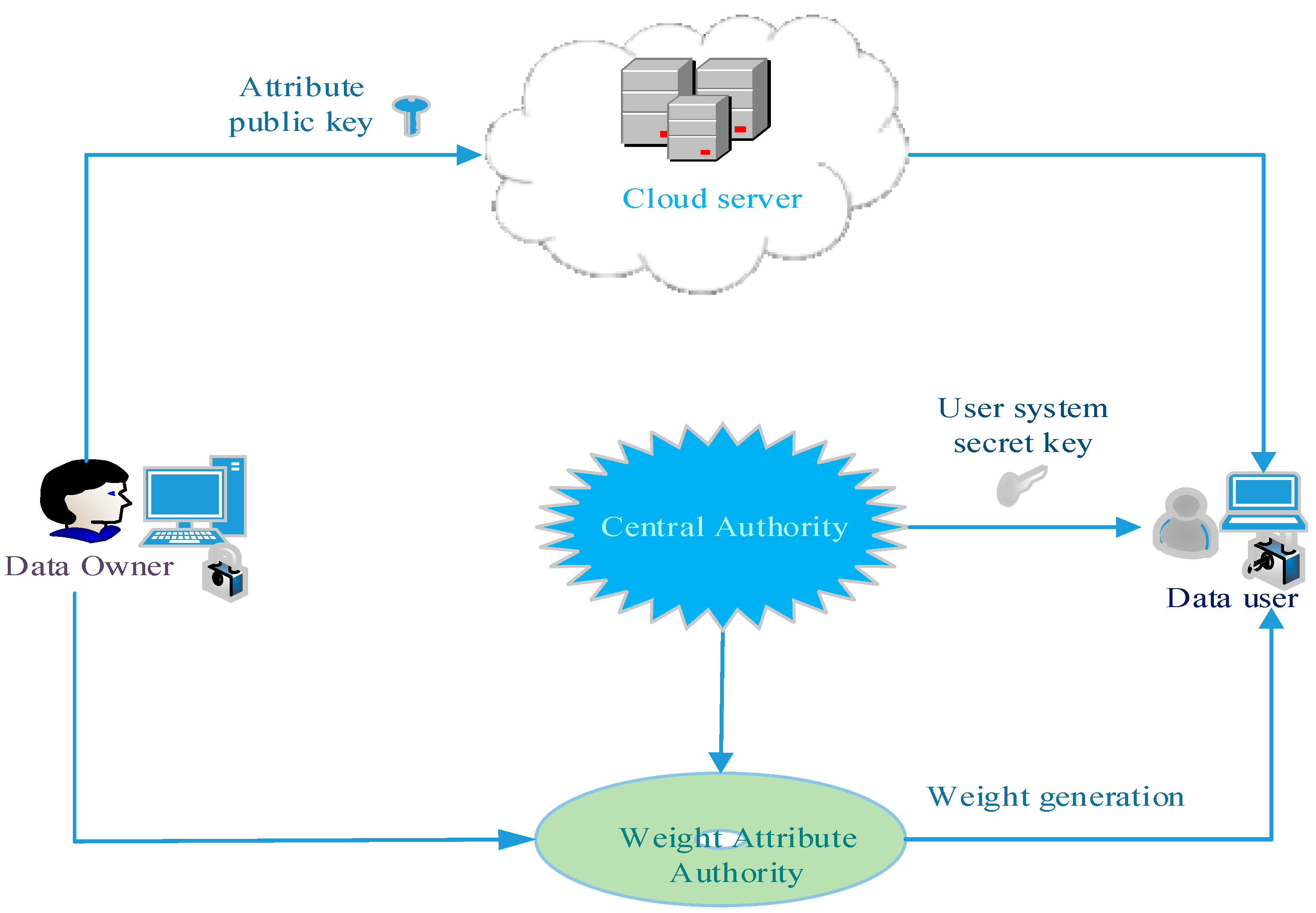
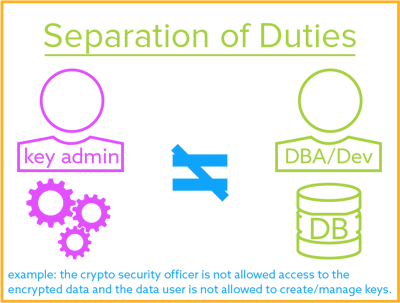
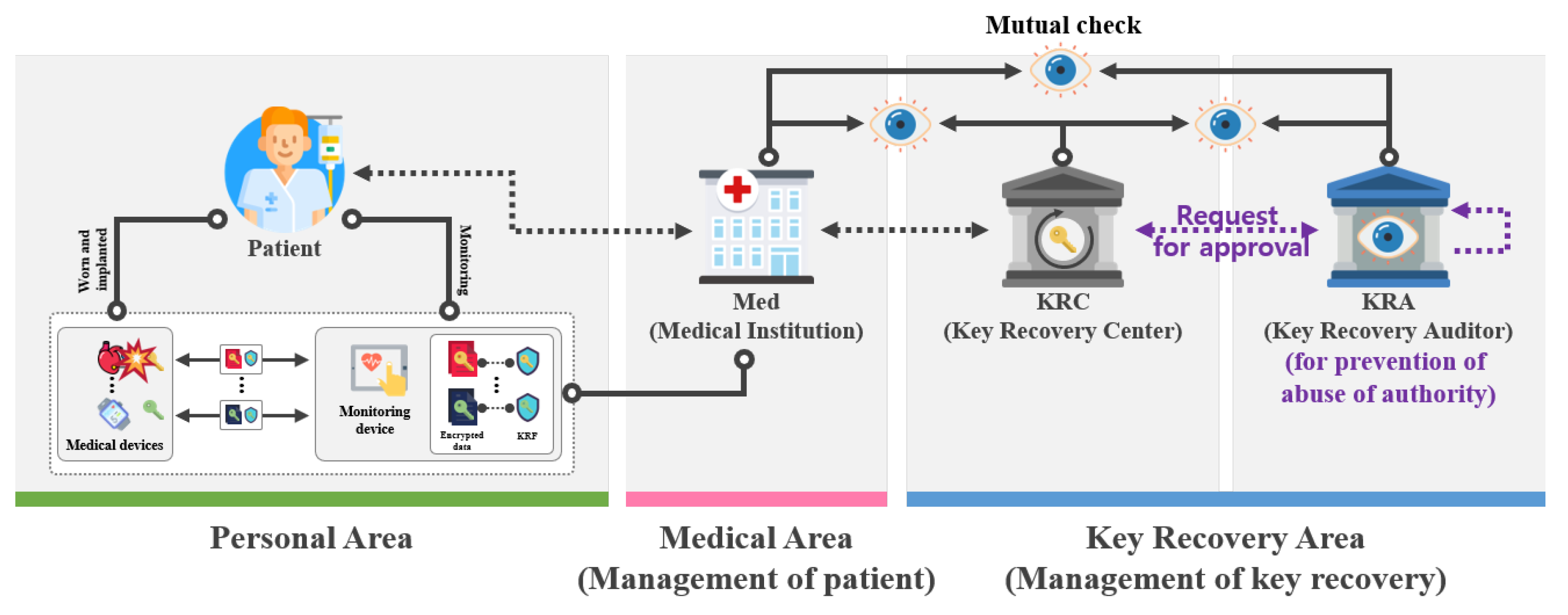
Much like a valet or coat check each key is stored in relation to the user that leverages it and then returned once queried. A key escrow encryption system or simply escrowed encryption system is an encryption system with a backup decryption capability that allows authorized persons users officers of an organization and government officials under certain prescribed conditions to decrypt ciphertext with the help of information supplied by one or more trusted parties who hold special data recovery keys. Unless stated differently in the contract only personal property may be removed from the property.
Ring 2 is used for drivers and protocols. Public keys and shared keys should never be used to encrypt this type of information. Which of the following is NOT a signaling protocol.
Option B is correct because 16 divided by 3 equals 5 with a remainder value of 1. HEDIS is designed to collect. The Correct Answer is- B.
As opposed to escrow recovery agents are typically used to. The broker must conduct the escrow personally and. The test is performed against the wrong host.
Whisker is a popular tool for _____. 1 Which of the following is not a type of symmetric-key cryptography technique.
Knowledge application - employ your knowledge to answer questions about components of real.
It is important to note that many modern operating systems do not fully implement this model. Which version of SNMP allows the manager to have a different shared secret with each agent. Is voidable if all parties agree to a mistake of contract. A voidable contract is best defined as which of the following. In the 1940s a team of cryptanalysts from the United States successfully broke a Soviet code based on a one-time pad in a project known as VENONA. Administrative claims and health record review data. User-level programs and applications run at Ring 3. A System administrators should retain user accounts after an employee has been terminated. Data Encryption Standard DES Diffie Hellman cipher.
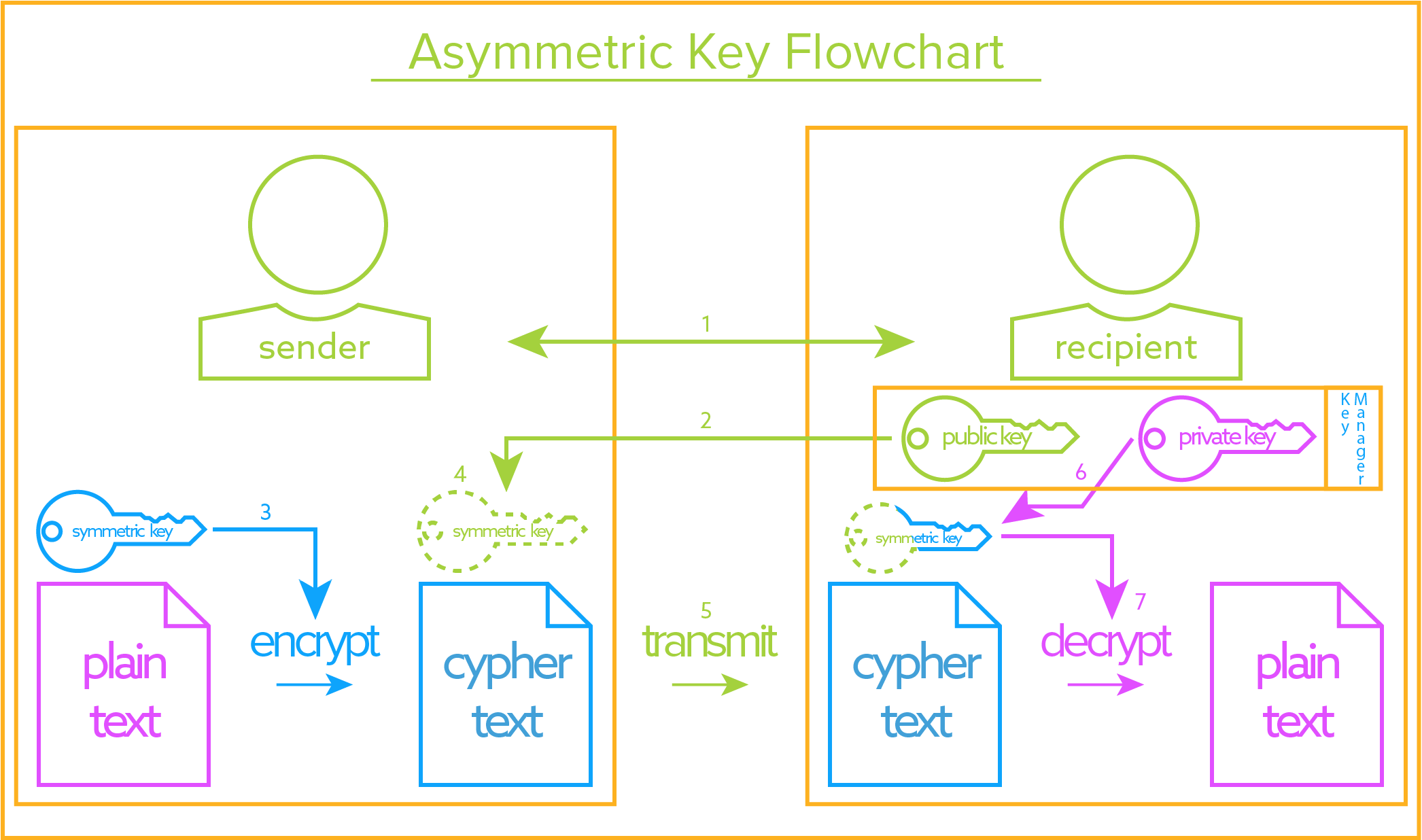
A voidable contract is best defined as which of the following. Which of the following is NOT a signaling protocol. A private key should be used to encrypt the signature of an e-mail in an asymmetric system such as PKI. A key escrow encryption system or simply escrowed encryption system is an encryption system with a backup decryption capability that allows authorized persons users officers of an organization and government officials under certain prescribed conditions to decrypt ciphertext with the help of information supplied by one or more trusted parties who hold special data recovery keys. The broker must conduct the escrow personally and. Public keys and shared keys should never be used to encrypt this type of information. Each key stored in an escrow system is tied to the original user and subsequently encrypted for security purposes.




























Post a Comment for "Which Of The Following Is Not A Component Of A Key Escrow System?"